LDAP + Multi-Factor Authentication (MFA) Integration
Cybertel MCX Application Server (MCX AS) integrates securely with Microsoft Active Directory (AD) via Secure LDAP (LDAPS) to enable Single Sign-On (SSO), automatic user provisioning and group-based role mapping.
The system also supports Multi-Factor Authentication (MFA) to add an additional layer of login security for administrators and users.
This dual integration ensures that only verified users can access critical communication services, leveraging existing enterprise IT infrastructure while enhancing security and operational efficiency.
Key Capabilities
| Function | Description |
|---|---|
| SSO via Active Directory | Login using existing AD credentials (username/password) |
| Automated Provisioning | AD group membership drives user creation and role assignment |
| Encrypted LDAPS | All user authentication and directory queries are encrypted |
| Multi-Factor Authentication | Supports SMS-based OTP and Microsoft Azure MFA |
| Policy-Based Control | MFA can be enabled per user or group with configurable PIN rules |
Benefits
- Centralized access control using Active Directory
Enforced MFA using secure methods (OTP, Authenticator App, Push Notification)
- Automatic user creation and deletion based on AD group membership
- Compliance with enterprise security frameworks (e.g., NIST, ISO)
- Real-time access revocation via AD account status
Use Cases
- Central login for MCPTT mobile clients and dispatch consoles
- Dispatcher authentication with SMS OTP from remote locations
- Azure MFA approval for PTT service access
- SSO + 2FA enforcement in large-scale enterprise deployments
- Alarm notifications for provisioning failures (e.g., license limits)
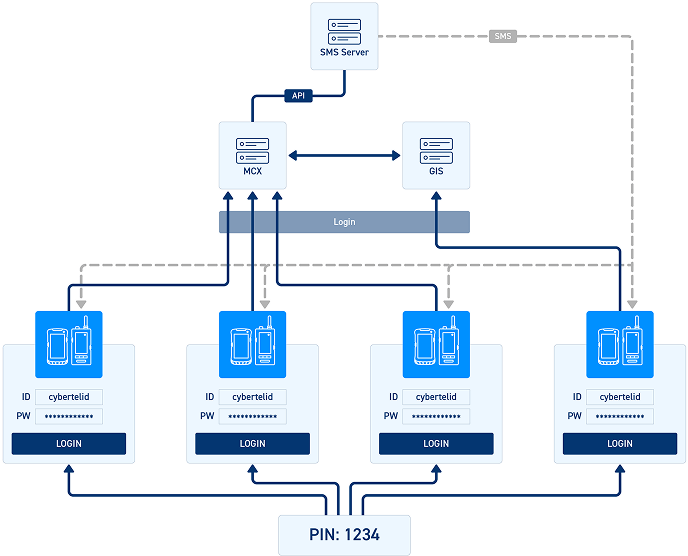
Authentication Workflows
-
A. LDAP SSO Flow
- User opens MCPTT app or console
- Enters AD credentials
- MCX AS sends credentials to AD via LDAPS
- AD returns authentication result
- On success, MCX maps user to profile and grants access
-
B. SMS-Based MFA (via SMCC)
- User logs in (with username/password or SSO)
- MCX AS checks MFA status and generates OTP
- OTP sent via SMS gateway (e.g., SMCC)
- User enters PIN on login screen
- If valid, access is granted; else, denied
PIN expiration and retry attempts are configurable per user.
-
C. Azure AD MFA
- User logs in via AD (SSO)
Azure MFA policy is triggered
- User confirms via app or enters code
- On success, redirected to MCX service
MFA methods: Authenticator App, Push Notification, or SMS fallback.
System Architecture
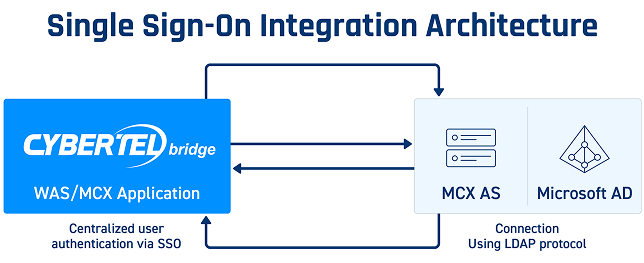
| Component | Role |
|---|---|
| MCX AS | Authenticates users, generates OTP, provisions roles |
| WAS (Web Admin Server) | Manages login flow, AD mappings, PIN input |
| Active Directory / Azure AD | Manages user identity and MFA policy |
| SMS Gateway (e.g., SMCC) | Sends OTPs to user devices (MSISDN) |
Organizational Structure Mapping
- Supports multi-tier hierarchy: Tenant > Admin > Unit > Operator
- AD group → MCX talk group mapping
- Nested groups and domain filters supported
- Group aliases (e.g., CN → Group ID) supported
Security & Compatibility
- Full LDAPS encryption (port 636)
- Compliant with enterprise IT and cybersecurity policies
Supports nested AD groups, user roles and Azure MFA
- Automatic logout if AD account is disabled or locked
- PIN invalidation on logout or timeout
Recording & Permissions
- AD group "supervisors" can access associated recordings
- Group name–based search on the recording server
- Web access via Chrome, Edge, or Firefox
Why Choose Cybertel for LDAP + MFA?
- Secure, scalable LDAP-based authentication with MFA
Seamless Microsoft Azure MFA support
- Dual login mode: LDAP + 2FA or local + 2FA
- Trusted in large-scale deployments across public safety and utilities


